-
Hackers Used Snappybee Malware and Citrix Flaw to Breach European Telecom Network

Oct 21, 2025Ravie LakshmananCyber Espionage / Network Security A European telecommunications organization is said to have been targeted by a threat actor that aligns with a China-nexus cyber espionage group known as Salt Typhoon. The organization, per Darktrace, was targeted in the first week of July 2025, with the attackers exploiting a Citrix NetScaler Gateway…
-
Google Identifies Three New Russian Malware Families Created by COLDRIVER Hackers
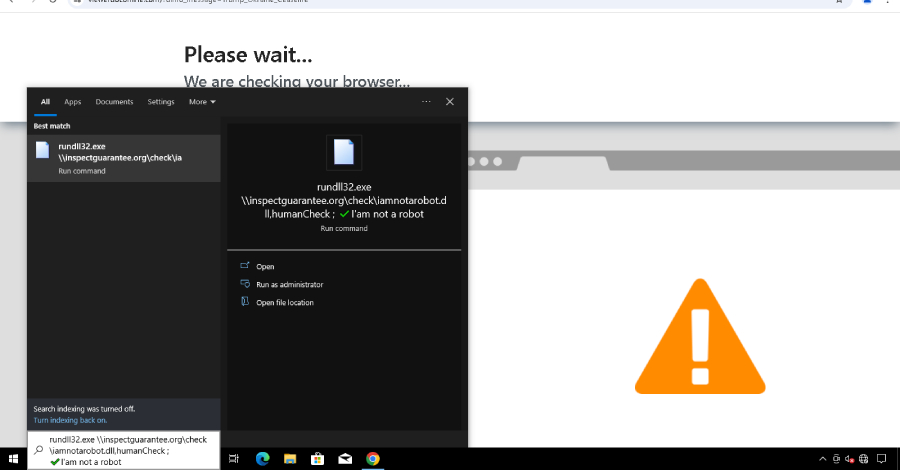
Oct 21, 2025Ravie LakshmananCyber Espionage / Threat Intelligence A new malware attributed to the Russia-linked hacking group known as COLDRIVER has undergone numerous developmental iterations since May 2025, suggesting an increased “operations tempo” from the threat actor. The findings come from Google Threat Intelligence Group (GTIG), which said the state-sponsored hacking crew has rapidly refined…
-
Securing AI to Benefit from AI

Artificial intelligence (AI) holds tremendous promise for improving cyber defense and making the lives of security practitioners easier. It can help teams cut through alert fatigue, spot patterns faster, and bring a level of scale that human analysts alone can’t match. But realizing that potential depends on securing the systems that make it possible. Every…
-
PolarEdge Targets Cisco, ASUS, QNAP, Synology Routers in Expanding Botnet Campaign
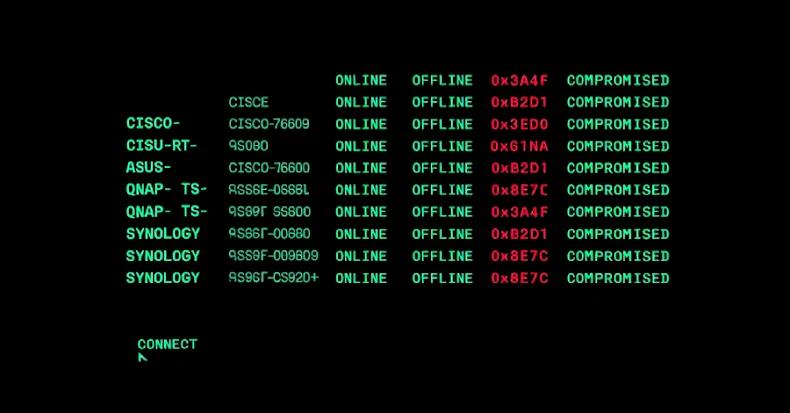
Oct 21, 2025Ravie LakshmananMalware / Vulnerability Cybersecurity researchers have shed light on the inner workings of a botnet malware called PolarEdge. PolarEdge was first documented by Sekoia in February 2025, attributing it to a campaign targeting routers from Cisco, ASUS, QNAP, and Synology with the goal of corralling them into a network for an as-yet-undetermined…
-
Meta Rolls Out New Tools to Protect WhatsApp and Messenger Users from Scams
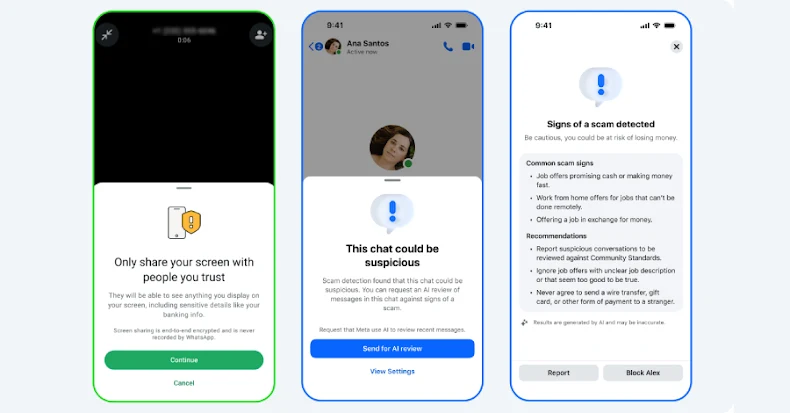
Oct 21, 2025Ravie LakshmananCryptocurrency / Encryption Meta on Tuesday said it’s launching new tools to protect Messenger and WhatsApp users from potential scams. To that end, the company said it’s introducing new warnings on WhatsApp when users attempt to share their screen with an unknown contact during a video call so as to prevent them…
-
TP-Link Patches Four Omada Gateway Flaws, Two Allow Remote Code Execution

Oct 22, 2025Ravie LakshmananVulnerability / Network Security TP-Link has released security updates to address four security flaws impacting Omada gateway devices, including two critical bugs that could result in arbitrary code execution. The vulnerabilities in question are listed below – CVE-2025-6541 (CVSS score: 8.6) – An operating system command injection vulnerability that could be exploited…
-
TARmageddon Flaw in Async-Tar Rust Library Could Enable Remote Code Execution
Oct 22, 2025Ravie LakshmananVulnerability / Data Protection Cybersecurity researchers have disclosed details of a high-severity flaw impacting the popular async-tar Rust library and its forks, including tokio-tar, that could result in remote code execution under certain conditions. The vulnerability, tracked as CVE-2025-62518 (CVSS score: 8.1), has been codenamed TARmageddon by Edera, which discovered the issue…
-
Researchers Identify PassiveNeuron APT Using Neursite and NeuralExecutor Malware

Oct 22, 2025Ravie LakshmananCyber Espionage / Network Security Government, financial, and industrial organizations located in Asia, Africa, and Latin America are the target of a new campaign dubbed PassiveNeuron, according to findings from Kaspersky. The cyber espionage activity was first flagged by the Russian cybersecurity vendor in November 2024, when it disclosed a set of…
-
Why You Should Swap Passwords for Passphrases

Oct 22, 2025The Hacker NewsData Breach / Enterprise Security The advice didn’t change for decades: use complex passwords with uppercase, lowercase, numbers, and symbols. The idea is to make passwords harder for hackers to crack via brute force methods. But more recent guidance shows our focus should be on password length, rather than complexity. Length…
-
Fake Nethereum NuGet Package Used Homoglyph Trick to Steal Crypto Wallet Keys

Oct 22, 2025Ravie LakshmananCryptocurrency / Software Integrity Cybersecurity researchers have uncovered a new supply chain attack targeting the NuGet package manager with malicious typosquats of Nethereum, a popular Ethereum .NET integration platform, to steal victims’ cryptocurrency wallet keys. The package, Netherеum.All, has been found to harbor functionality to decode a command-and-control (C2) endpoint and exfiltrate…
Search
About
Lorem Ipsum has been the industrys standard dummy text ever since the 1500s, when an unknown prmontserrat took a galley of type and scrambled it to make a type specimen book.
Lorem Ipsum has been the industrys standard dummy text ever since the 1500s, when an unknown prmontserrat took a galley of type and scrambled it to make a type specimen book. It has survived not only five centuries, but also the leap into electronic typesetting, remaining essentially unchanged.
Archive
Categories
Recent Posts
Tags
Gallery