-
CISA Flags Adobe AEM Flaw with Perfect 10.0 Score — Already Under Active Attack

Oct 16, 2025Ravie LakshmananVulnerability / Data Security The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Wednesday added a critical security flaw impacting Adobe Experience Manager to its Known Exploited Vulnerabilities (KEV) catalog, based on evidence of active exploitation. The vulnerability in question is CVE-2025-54253 (CVSS score: 10.0), a maximum-severity misconfiguration bug that could result…
-
$15B Crypto Bust, Satellite Spying, Billion-Dollar Smishing, Android RATs & More

Oct 16, 2025Ravie LakshmananCybersecurity / Hacking News The online world is changing fast. Every week, new scams, hacks, and tricks show how easy it’s become to turn everyday technology into a weapon. Tools made to help us work, connect, and stay safe are now being used to steal, spy, and deceive. Hackers don’t always break…
-
Beware the Hidden Costs of Pen Testing

Penetration testing helps organizations ensure IT systems are secure, but it should never be treated in a one-size-fits-all approach. Traditional approaches can be rigid and cost your organization time and money – while producing inferior results. The benefits of pen testing are clear. By empowering “white hat” hackers to attempt to breach your system using…
-
Hackers Deploy Linux Rootkits via Cisco SNMP Flaw in ‘Zero Disco’ Attacks
Oct 16, 2025Ravie LakshmananVulnerability / Linux Cybersecurity researchers have disclosed details of a new campaign that exploited a recently disclosed security flaw impacting Cisco IOS Software and IOS XE Software to deploy Linux rootkits on older, unprotected systems. The activity, codenamed Operation Zero Disco by Trend Micro, involves the weaponization of CVE-2025-20352 (CVSS score: 7.7),…
-
How to Assess and Choose the Right AI-SOC Platform

Scaling the SOC with AI – Why now? Security Operations Centers (SOCs) are under unprecedented pressure. According to SACR’s AI-SOC Market Landscape 2025, the average organization now faces around 960 alerts per day, while large enterprises manage more than 3,000 alerts daily from an average of 28 different tools. Nearly 40% of those alerts go…
-
LinkPro Linux Rootkit Uses eBPF to Hide and Activates via Magic TCP Packets

Oct 16, 2025Ravie LakshmananVulnerability / Malware An investigation into the compromise of an Amazon Web Services (AWS)-hosted infrastructure has led to the discovery of a new GNU/Linux rootkit dubbed LinkPro, according to findings from Synacktiv. “This backdoor features functionalities relying on the installation of two eBPF [extended Berkeley Packet Filter] modules, on the one hand…
-
Hackers Abuse Blockchain Smart Contracts to Spread Malware via Infected WordPress Sites
A financially motivated threat actor codenamed UNC5142 has been observed abusing blockchain smart contracts as a way to facilitate the distribution of information stealers, such as Atomic (AMOS), Lumma, Rhadamanthys (aka RADTHIEF), and Vidar, targeting both Windows and Apple macOS systems. “UNC5142 is characterized by its use of compromised WordPress websites and ‘EtherHiding,’ a technique…
-
North Korean Hackers Use EtherHiding to Hide Malware Inside Blockchain Smart Contracts

Oct 16, 2025Ravie LakshmananMalware / Blockchain A threat actor with ties to the Democratic People’s Republic of Korea (aka North Korea) has been observed leveraging the EtherHiding technique to distribute malware and enable cryptocurrency theft, marking the first time a state-sponsored hacking group has embraced the method. The activity has been attributed by Google Threat…
-
Microsoft Revokes 200 Fraudulent Certificates Used in Rhysida Ransomware Campaign

Oct 17, 2025Ravie LakshmananMalware / Cybercrime Microsoft on Thursday disclosed that it revoked more than 200 certificates used by a threat actor it tracks as Vanilla Tempest to fraudulently sign malicious binaries in ransomware attacks. The certificates were “used in fake Teams setup files to deliver the Oyster backdoor and ultimately deploy Rhysida ransomware,” the…
-
Researchers Uncover WatchGuard VPN Bug That Could Let Attackers Take Over Devices
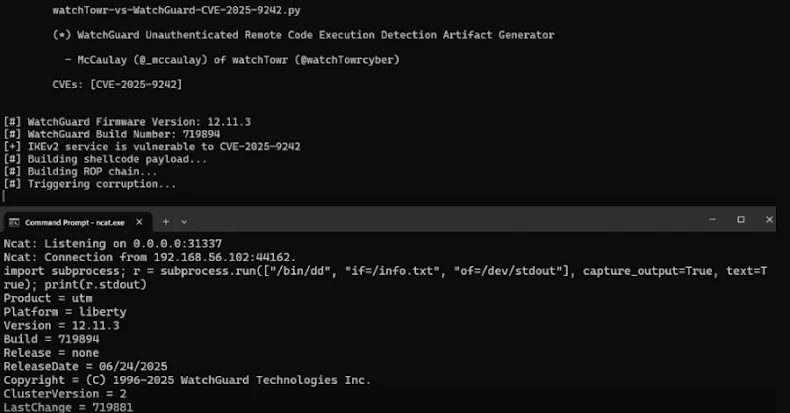
Oct 17, 2025Ravie LakshmananVulnerability / VPN Security Cybersecurity researchers have disclosed details of a recently patched critical security flaw in WatchGuard Fireware that could allow unauthenticated attackers to execute arbitrary code. The vulnerability, tracked as CVE-2025-9242 (CVSS score: 9.3), is described as an out-of-bounds write vulnerability affecting Fireware OS 11.10.2 up to and including 11.12.4_Update1,…
Search
About
Lorem Ipsum has been the industrys standard dummy text ever since the 1500s, when an unknown prmontserrat took a galley of type and scrambled it to make a type specimen book.
Lorem Ipsum has been the industrys standard dummy text ever since the 1500s, when an unknown prmontserrat took a galley of type and scrambled it to make a type specimen book. It has survived not only five centuries, but also the leap into electronic typesetting, remaining essentially unchanged.
Archive
Categories
Recent Posts
Tags
Gallery